Secure Your AWS Infrastructure: Key Best Practices for Safety
Written on
Chapter 1: Understanding Cloud Infrastructure Security
In today's digital landscape, having a cloud infrastructure is essential for businesses of all sizes. Cloud computing provides numerous advantages, including scalability, enhanced security, and improved performance, allowing organizations to pay solely for the services they utilize. This trend is not only embraced by large enterprises but also by small businesses and startups that may lack the resources to establish an extensive in-house infrastructure. The myriad benefits offered by cloud services make them increasingly appealing. However, due to their sophisticated design and functionality, these services can be vulnerable if not managed properly. Fortunately, many cloud service providers have established best practices to help businesses create secure architectures.
This article will delve into critical AWS services and their security considerations. AWS infrastructure security operates on a shared responsibility model, where Amazon delineates the security aspects it manages and those that organizations must handle based on their specific needs. For instance, AWS is tasked with safeguarding the infrastructure on which its services run, while organizations are responsible for securing their implementations within that framework.
Section 1.1: AWS EC2 Service Overview
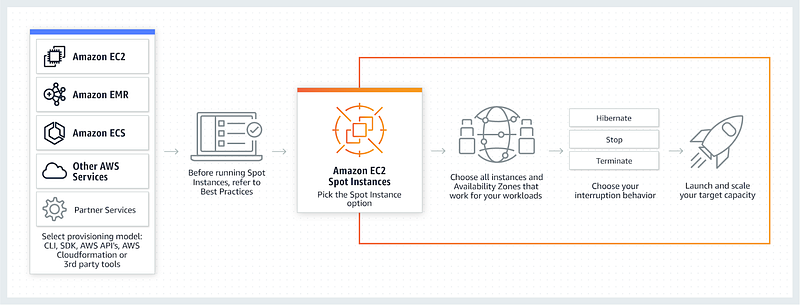
AWS EC2 (Elastic Compute Cloud) offers virtual servers that enable users to run applications on the AWS platform. These virtual servers, known as EC2 instances, provide a flexible computing environment, allowing organizations to scale resources according to application demands. AWS's ability to adapt resources underscores its scalability, and it can supply numerous EC2 instances to ensure optimal performance.
AWS categorizes EC2 instances based on factors such as CPU, memory, storage, and networking capacity. The extensive scope of EC2 allows organizations to tailor their usage based on specific requirements. Here are some best practices for managing EC2 instances:
Port Access Restrictions
EC2 features security groups that control communication between instances. Regularly monitor IP addresses and open ports within security groups to prevent unauthorized access. Publicly accessible ports may pose significant security risks.
Managing Unused Key Pairs
Amazon provides various login methods, including Key Pairs, which consist of public and private keys. To enhance security, identify and remove any unused key pairs that could lead to vulnerabilities.
Section 1.2: IAM (Identity Access Management)
IAM is crucial for creating users and managing their permissions, enabling secure access to AWS resources. For instance, granting a user read-only access to an S3 bucket ensures they cannot modify its contents.
Removing Inactive Users
Regularly review user accounts to eliminate those who are no longer active within the organization. This practice reduces the attack surface and potential security breaches.
Key Rotation
Regularly rotating IAM access keys is vital to mitigate the risk of compromised credentials and inadvertent exposures.
Chapter 2: Safeguarding S3 Buckets
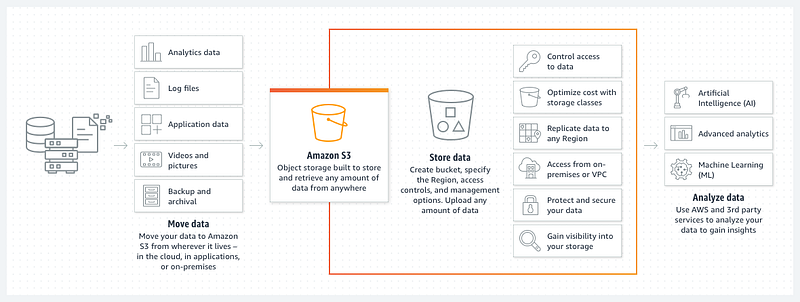
S3 (Simple Storage Service) allows for the storage and retrieval of vast amounts of data. With features like versioning, S3 buckets can help recover from accidental deletions. After creating a bucket, users should configure access policies to align with organizational needs.
Implementing Server-Side Encryption
S3 buckets must utilize server-side encryption (SSE) to protect sensitive data at rest. This feature encrypts data upon storage and decrypts it upon user request, ensuring secure access.
Avoiding Public Access
Ensure that public buckets do not have full control access enabled to prevent unauthorized changes or data theft. Regularly check the permissions and access control lists for your S3 buckets.
Hands-On With AWS Security Best Practices - This video offers practical insights into essential security measures for AWS, focusing on protecting your infrastructure.
Essential AWS Security Best Practices: Building Workloads the Well-Architected Way - This video discusses best practices for building secure and reliable AWS workloads.
Conclusion
As the adoption of cloud infrastructure accelerates, so does the need for robust security measures. When implementing AWS services, adhering to established best practices is crucial for protecting both data and infrastructure. While additional practices may exist, the priority of their implementation ultimately depends on the organization’s specific security goals.