Understanding the Pyramid of Pain in Cyber Threat Intelligence
Written on
Introduction to the Pyramid of Pain
In the realm of Cyber Threat Intelligence, various models have emerged, each with its own set of strengths and weaknesses. Among them, the Pyramid of Pain stands out as a widely recognized framework within the Threat Hunting community. This model serves as an excellent starting point for anyone interested in delving into the world of Threat Hunting.
When an attacker bypasses your security measures or attempts to evade detection, you may uncover evidence or artifacts indicating their actions. These forensic artifacts are referred to as indicators of compromise (IoCs).
Initially introduced by David J. Bainco in 2013, the Pyramid of Pain illustrates the types of artifacts that can be discovered during an attack and the corresponding challenges these artifacts pose to the adversary when they are denied access. Bainco emphasizes that not all IoCs carry the same weight; the impact of blocking different artifacts can vary significantly.
As you ascend the layers of the pyramid and successfully deny access to various indicators, the adversary experiences increasing difficulty in executing their attack.
Video Description: This tutorial on the Pyramid of Pain provides a comprehensive overview of the model and its application in threat hunting.
Hash Values
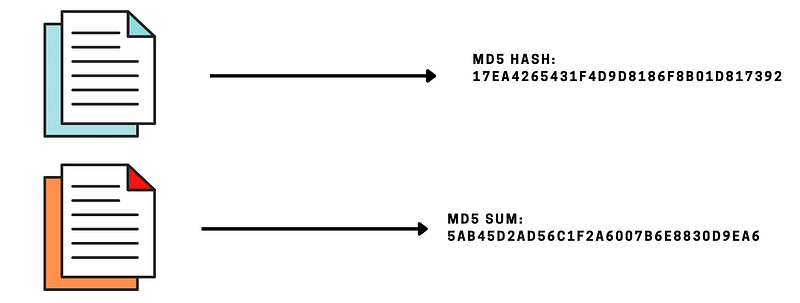
At the foundational layer, hash values play a crucial role in identifying specific malware samples. You can locate the hash values of files on your device and utilize various online tools to verify if any match known malware signatures. However, attackers can easily modify their code to generate new hashes, allowing them to slip through detection mechanisms with minimal difficulty.
IP Addresses
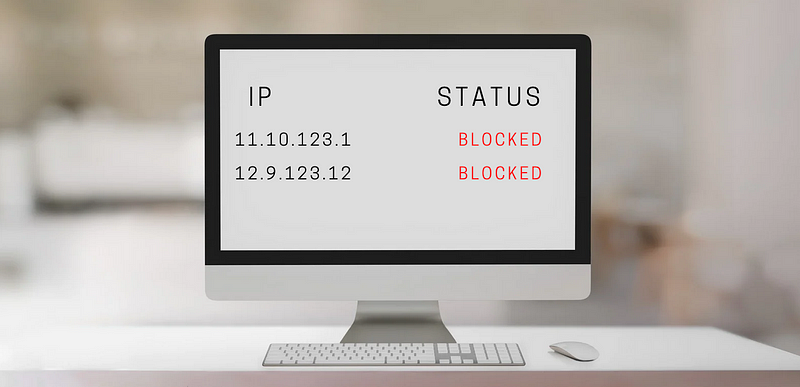
Blocking access to specific IP addresses forces attackers to either change their address, acquire a new one, or resort to using VPNs or proxy networks, complicating their efforts and consuming valuable time.
Domain Names
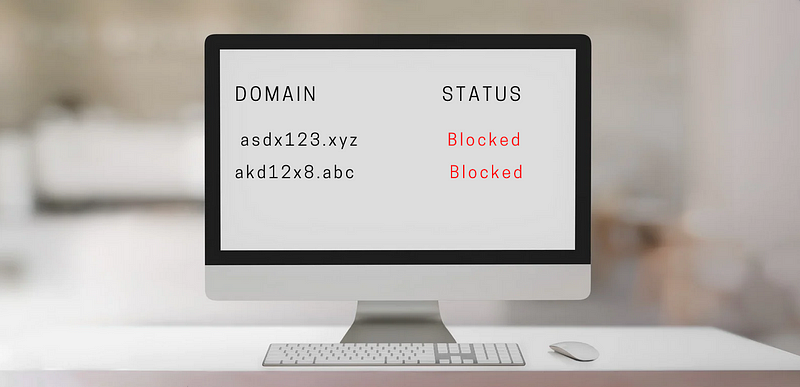
Domain names, which map directly to IP addresses, present a unique challenge when it comes to modification. Altering a domain name can take anywhere from a few hours to a full day, adding to the attacker’s frustration.
Network and Host Artifacts
User-Agent Strings can be utilized to differentiate between attackers and legitimate users. Attackers often employ specific tools that can be identified through their names in system logs. For instance, if an attacker uses Nmap to scan your network, it may appear in your log files, providing you with evidence to block requests from any host associated with that tool.
Tools
Denying access to tools installed on the attacker’s machine may force them to either develop new tools from scratch, upload their existing ones, or abandon the network entirely, significantly impeding their operations.
Tactics, Techniques, and Procedures (TTPs)
Before delving into this section, it’s essential to understand what TTPs are. TTP stands for Tactics, Techniques, and Procedures, which are distinctive patterns employed by adversaries to compromise their targets. Essentially, TTPs reveal the behavioral fingerprints of attackers, enabling you to trace the source of an attack by analyzing their methods.
Identifying an adversary's TTPs can allow you to preemptively thwart attacks. For further insights, refer to MITRE's ATT&CK framework, which provides valuable information on TTPs.
Conclusion
The Pyramid of Pain is an invaluable concept for Threat Hunters, Incident Responders, and SOC analysts. Its application is recognized by leading cybersecurity companies, including Cisco Security and SentinelOne.
Video Description: Explore Cisco's approach to aligning security strategies with the Pyramid of Pain in this informative overview.